.jpg)
Today Biometric technologies are used for identification and verification purposes in many industries and applications to provide secure access. This paper describes on how we can utilize various biometrics for the automobiles, replacing the traditional key fob while integrating other functionalities to enhance the user experience and maintain/enhance security.
Read More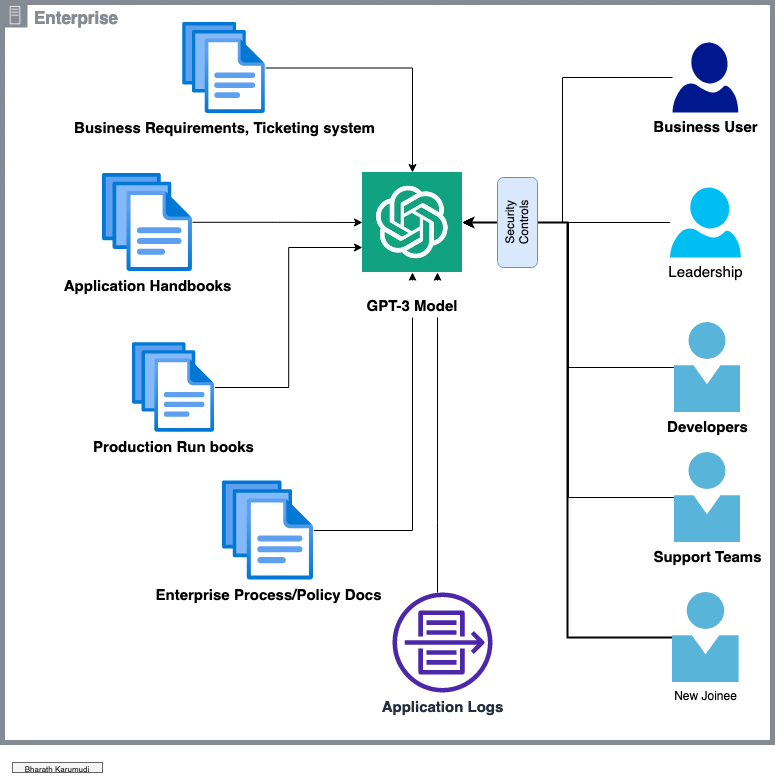
As many individuals and enterprises are playing with the ChatGPT with different questions, I was thinking about how it can help an enterprise to solve our day to day problems and save time in finding the correct information. Below is a high level thought on how we can leverage the GPT-3 model for enterprise.
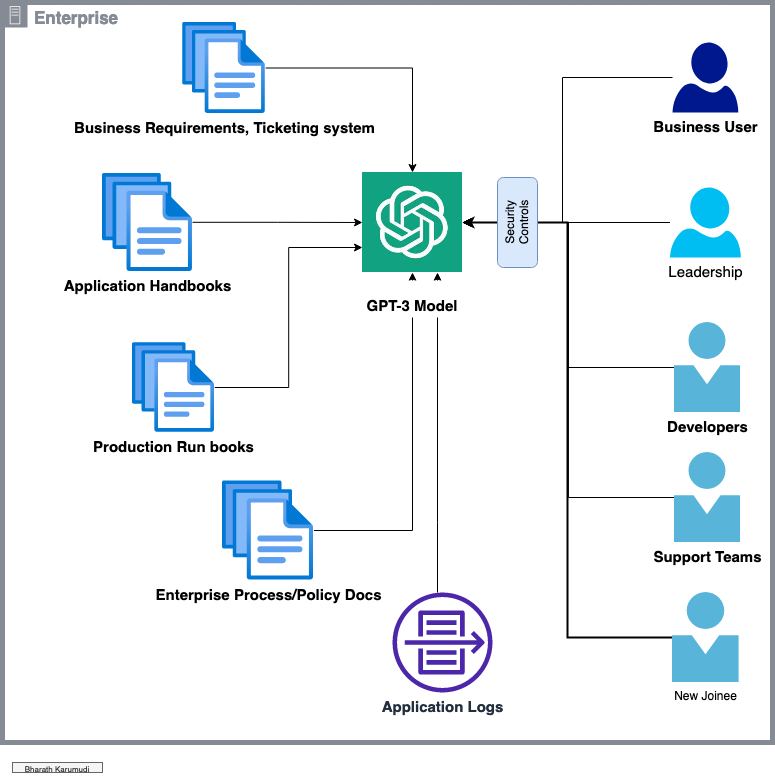
In today’s fast-paced business environment, having quick and easy access to the information you need is more important than ever. However, with so much data being generated and stored in various systems, it can be difficult to find what you’re looking for. That’s where GPT-3 comes in.
GPT-3, also known as Generative Pre-trained Transformer 3, is a state-of-the-art language generation model developed by OpenAI. It is capable of understanding and generating human-like text, with a high degree of fluency and coherence. By integrating GPT-3 with your enterprise systems and data, you can provide business users, developers, and new employees with quick and easy access to the information they need.
One of the main advantages of this approach is that it can save time and effort for users who would otherwise have to manually search through multiple sources of information. It can also provide them with a more intuitive and user-friendly way of accessing the information they need.
For example, imagine being able to ask GPT-3 about the performance of a specific application, and it providing you with real-time data and insights. Developers can use it to troubleshoot issues and understand how their apps are running. And new employees can use it to learn about enterprise processes and policies.
GPT-3 can also help with automating repetitive tasks, such as creating runbooks and application handbooks, as well as summarizing log files and providing summaries of important events.
But that’s not all! By integrating GPT-3 with your ticketing system, it can also help with resolving customer issues and providing quick solutions.
However, it’s important to keep in mind that GPT-3, like any AI model, is only as good as the data it’s been trained on, so it is important to ensure that the data fed to GPT-3 is accurate, comprehensive, and up-to-date. Additionally, it’s also important to consider the security and privacy aspect of the data, as GPT-3 will be handling sensitive information.
Overall, integrating GPT-3 with your enterprise systems and data has the potential to revolutionize the way you access and manage your data. It can save time, effort and improve the user experience, but it will require careful planning and implementation to ensure that it delivers the desired results.
In conclusion, GPT-3 can be a powerful tool for enterprise data management, and it’s worth considering it as part of your organization’s strategy to improve data management and access.
Read More
Antivirus and malware detection software primarily used in signature-based approach. These software’s use a set of rules from a library, based on previously known malware and published vulnerabilities from the software manufacturer. The rules are very specific to the vulnerability and malware, thus making them brittle and very context and malware specific. So a new malware release still has the potential to take advantage of the same vulnerability that has already been addressed for different malware. The Antivirus software provider releases updates to the library of rules on a periodic basis, or as critical vulnerabilities are discovered. One risk with the traditional Antivirus or malware detection software is zero-day vulnerabilities, where the hackers discover it before either the software manufacturer or the antivirus provider.
Read More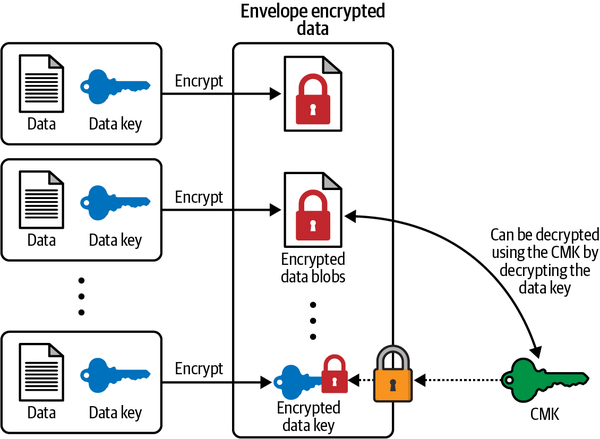
Envelope encryption is a method of encrypting data where the data is encrypted using a symmetric key, and the symmetric key is then encrypted using an asymmetric key. The encrypted data and encrypted symmetric key are referred to as the “envelope.”
The advantage of this approach is that the asymmetric key, which is typically used to encrypt the symmetric key, is much slower to use for encrypting and decrypting large amounts of data compared to the symmetric key. This means that the data can be quickly encrypted and decrypted using the symmetric key, while the slower asymmetric key is used only to secure the symmetric key. This makes envelope encryption particularly useful for protecting sensitive data, as it allows for fast and efficient encryption and decryption of large amounts of data without sacrificing security.
Envelope encryption is often used to secure sensitive data in cloud environments, where the data may need to be accessed by multiple parties but the security of the data key cannot be guaranteed. It provides an additional layer of security by ensuring that only authorized parties can decrypt the data, even if the data key itself is compromised.
+--------+ +--------+
| | | |
| User | | KMS |
| | | |
+--------+ +--------+
| |
(Encryption) | Generate data key (DEK) |
|---------------------------->
| |
| DEK (plaintext and |
| ciphertext) |
|<----------------------------
| |
| Encrypt data with DEK |
|---------------------------->
| |
| Encrypted data and |
| ciphertext DEK |
|<----------------------------
| |
| Store encrypted data and |
| ciphertext DEK |
|---------------------------->
| |
| Discard plaintext DEK |
|<----------------------------
| |
(Decryption) | Retrieve ciphertext DEK |
| and encrypted data |
|---------------------------->
| |
| Obtain plaintext DEK by |
| decrypting ciphertext DEK |
|---------------------------->
| |
| Plaintext DEK |
|<----------------------------
| |
| Decrypt data with |
| plaintext DEK |
|---------------------------->
| |
| Decrypted data |
|<----------------------------
'''
Usage: Python code to demonstrate the implementation on Envelope Encryption using AWS KMS
Before running this code, configure AWS Credentials in your environment:
$ export AWS_ACCESS_KEY_ID=
$ export AWS_SECRET_ACCESS_KEY=
Written on Dec/28/2022
Permalink: https://gist.github.com/bharathkarumudi/6a6b8836c827d846167381d3ba42974d
'''
# Importing required libraries
import boto3
from Cryptodome.Random import get_random_bytes
from Cryptodome.Cipher import AES
from Cryptodome.Util.Padding import pad, unpad
import base64
# Setting the region
region = 'us-east-1'
# Create the KMS client
kms_client = boto3.client('kms', region_name=region)
def encrypt_data(plaintext, key_id):
'''
Method to encrypt the data using envelope encryption
The method returns encrypted data, encrypted data key, and also respective base64 encoded values.
'''
# Generate a data key using AWS CMK
data_key = kms_client.generate_data_key(KeyId=key_id, KeySpec='AES_256')
plaintext_data_key = data_key['Plaintext']
encrypted_data_key = data_key['CiphertextBlob']
# Generate a random IV
iv = get_random_bytes(16)
# Encrypt the data with AES CBC mode
cipher = AES.new(plaintext_data_key, AES.MODE_CBC, iv)
padded_data = pad(plaintext, 16)
ciphertext_blob = cipher.encrypt(padded_data)
# Encode the encrypted data and data key with base64
encoded_ciphertext_blob = base64.b64encode(ciphertext_blob)
encoded_encrypted_data_key = base64.b64encode(encrypted_data_key)
# Return the encrypted data and the encrypted data key
return ciphertext_blob, encoded_ciphertext_blob, encrypted_data_key, encoded_encrypted_data_key, iv
def decrypt_data(encoded_ciphertext_blob, encoded_encrypted_data_key, iv):
'''
Method to decrypt the data
The method returns the decrypted data
'''
# Base64 decode of encrypted data and encrypted data key
decoded_ciphertext_blob = base64.b64decode(encoded_ciphertext_blob)
decoded_encrypted_data_key = base64.b64decode(encoded_encrypted_data_key)
# Decrypt the data key
data_key = kms_client.decrypt(CiphertextBlob=decoded_encrypted_data_key)
plaintext_data_key = data_key['Plaintext']
# Decrypt the data
cipher = AES.new(plaintext_data_key, AES.MODE_CBC, iv)
decrypted_padded_data = cipher.decrypt(decoded_ciphertext_blob)
plaintext = unpad(decrypted_padded_data, 16)
# Return the decrypted data
return plaintext
def main():
'''
Main method
'''
#AWS CMK Key ARN
key_id = ""
# Setting the plain text, which needs to be encrypted
input_plaintext = b"This is a confidential message which needs to be encrypted."
# Encrypting the data
ciphertext_blob, encoded_ciphertext_blob, encrypted_data_key, encoded_encrypted_data_key, iv = encrypt_data(input_plaintext, key_id)
# Decrypt the data
plaintext = decrypt_data(encoded_ciphertext_blob, encoded_encrypted_data_key, iv)
# Store the encrypted string and the encrypted data key in a file (optional)
with open('datastore.csv', 'w') as f:
f.writelines([str(encoded_ciphertext_blob) + ',', str(encoded_encrypted_data_key) + ',', str(iv)])
if __name__ == "__main__":
main()
Envelope encryption is a valuable tool for securing sensitive data in a variety of contexts, offering improved security, efficiency, and key management. By combining the speed of symmetric key encryption with the security of asymmetric key encryption, envelope encryption allows you to transfer large amounts of data quickly and securely.
Read More